
Dynamics

|
Generational Dynamics |
| Forecasting America's Destiny ... and the World's | |
| HOME WEB LOG COUNTRY WIKI COMMENT FORUM DOWNLOADS ABOUT | |
Hackers use Facebook to penetrate corporate networks
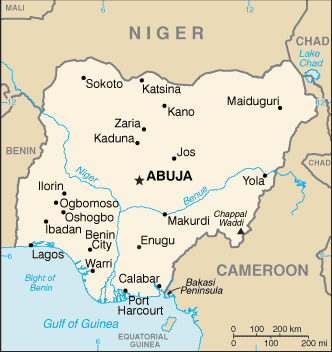 |
Hundreds of Christians were shot or hacked to death by Faluna Muslims on Sunday. According to the Times Online, they were targeted killings, thought to be revenge killings for Christian killings of Muslims in January. (See "20-Jan-10 News - Hundreds die in Muslim-Christian riots in Nigeria.")
Jos is in the middle of Nigeria, right on the fault line between Muslims who live in the north and Christians who live in the south.
Nigeria's last crisis war as the Nigerian civil war, or Biafran war, fought from 1967-69 between Muslims and Christians. It's now been over 40 years since that war ended, time enough for occasional spurts of renewed violence to occur, but not yet time enough for a full-scale civil war to begin again.
A really mind-blowing study has been conducted that shows how hackers, using information gleaned from Facebook, can penetrate an entire corporate computer network. The study is described in Dark Reading.
The company performing the study, Secure Network, actually performed these tests themselves, to prove how easy it is to hack into a corporate network.
They start by going to a Facebook site for company employees, and they harvest e-mail addresses and personal information about the employees. They get into the Facebook site by using a bogus identity, pretending to be an employee.
Then they set up a web site that looks like the company web site, but with a slightly different domain name, to make it look like a human resources web site. If the company web site is xyz.com, then the fake web site is xyz-company-benefits.com, for example.
They then send personal e-mail messages to the employees for whom they have e-mail addresses, directing them to log in to the fake web site using their company credentials.
Here's the amazing part: Nearly 50% of the employees who receiving these "spear-phishing" messages respond to the e-mail message by logging in to the fake web site with the logins and passwords that they use on their employer's network. The hackers can then collect this information, and use it to penetrate the network.
The more I learn about computer security, the more amazed I am about how easy it is for hackers to hack into people's computers. And it's not like you see on TV, where the CSI guy or the NCIS girl sits at a computer, types some clever commands, and breaks into a remote network in time for the next commercial. What you see on TV is simply impossible.
No, computer hacking works another way -- by fooling people, by using an ever-growing variety of tricks to get you to trust them into giving you the information they want. And Facebook is an ideal medium in which to gain your trust.
This is a good time to remind everyone that, from the point of view of Generational Dynamics, the great events can be neither caused nor prevented by politicians. Instead, they're caused by great masses of people, entire generations of people. Thus, for example, President Bush didn't make a serendipitous decision to make the ground invasion of 2003; he was forced to do it by public panic over weapons of mass destruction, and that Al Gore would have made the same decision if he'd been president after 9/11. (See: "The Iraq war may be related to the bombing of Hiroshima and Nagasaki.")
And during Barack Obama's presidential campaign, I was bitterly critical of his campaign promises that were blatantly absurd. He was going to heal the world with his mere presence -- cure global warming, provide universal health care, close Guantanamo, leave Iraq in peace, bring a two-state solution to Palestinians and Israelis, beat the Taliban in Afghanistan, restore the stock market bubble, and dismantle President Bush's war against terror. Nothing was beyond his reach. I indicated that he would fail at all of these objectives. This was just common sense.
Increasing, the loony left has been turning against Obama because he didn't magically heal the world like he promised. On Sunday, the ACLU purchased a full page ad in the NY Times:
 |
For some reason, the thought of Obama morphing into Bush strikes me as funny. If you'd like to read the text that accompanied the ad, see the press release from the ACLU web site.
Many on the loony left that got Obama elected are now viciously turning against him for not fulfilling his campaign promises, which could never have been fulfilled anyway. They really should cut him some slack, but then they wouldn't be loony, would they?
Greek Prime Minister George Papandreou is visiting Washington, and gave a speech calling for greater regulation of speculators, as if that were even possible. He said that Greece is not looking for money without cracking a smile. He said that if the Greek financial crisis worsens, then it would negatively affect the U.S., which is true. MarketWatch
There's talk among European officials to establish a new "European Monetary Fund," similar to the International Monetary Fund (IMF), except that it would be set up to bail out European countries like Greece. (Irish Times) However, other European officials are already shooting the idea down. (Reuters) From the point of view of Generational Dynamics, there will be plenty of great ideas and new proposals, but none of them will be adopted until after the Clash of Civilizations world war. Only at that time will people be willing to make the sacrifices necessary to prevent a new war from happening again.
News you can use: Women who drink moderately tend to gain less weight in midlife, though the same conclusion does not apply to heavier drinkers. LA Times
(Comments: For reader comments, questions and discussion,
see the 9-Mar-10 News - Muslims in revenge massacre against Nigeria Christians thread of the Generational Dynamics forum. Comments may
be posted anonymously.)
(9-Mar-2010)
Permanent Link
Receive daily World View columns by e-mail
Donate to Generational Dynamics via PayPal
Web Log Summary - 2016
Web Log Summary - 2015
Web Log Summary - 2014
Web Log Summary - 2013
Web Log Summary - 2012
Web Log Summary - 2011
Web Log Summary - 2010
Web Log Summary - 2009
Web Log Summary - 2008
Web Log Summary - 2007
Web Log Summary - 2006
Web Log Summary - 2005
Web Log Summary - 2004
Web Log - December, 2016
Web Log - November, 2016
Web Log - October, 2016
Web Log - September, 2016
Web Log - August, 2016
Web Log - July, 2016
Web Log - June, 2016
Web Log - May, 2016
Web Log - April, 2016
Web Log - March, 2016
Web Log - February, 2016
Web Log - January, 2016
Web Log - December, 2015
Web Log - November, 2015
Web Log - October, 2015
Web Log - September, 2015
Web Log - August, 2015
Web Log - July, 2015
Web Log - June, 2015
Web Log - May, 2015
Web Log - April, 2015
Web Log - March, 2015
Web Log - February, 2015
Web Log - January, 2015
Web Log - December, 2014
Web Log - November, 2014
Web Log - October, 2014
Web Log - September, 2014
Web Log - August, 2014
Web Log - July, 2014
Web Log - June, 2014
Web Log - May, 2014
Web Log - April, 2014
Web Log - March, 2014
Web Log - February, 2014
Web Log - January, 2014
Web Log - December, 2013
Web Log - November, 2013
Web Log - October, 2013
Web Log - September, 2013
Web Log - August, 2013
Web Log - July, 2013
Web Log - June, 2013
Web Log - May, 2013
Web Log - April, 2013
Web Log - March, 2013
Web Log - February, 2013
Web Log - January, 2013
Web Log - December, 2012
Web Log - November, 2012
Web Log - October, 2012
Web Log - September, 2012
Web Log - August, 2012
Web Log - July, 2012
Web Log - June, 2012
Web Log - May, 2012
Web Log - April, 2012
Web Log - March, 2012
Web Log - February, 2012
Web Log - January, 2012
Web Log - December, 2011
Web Log - November, 2011
Web Log - October, 2011
Web Log - September, 2011
Web Log - August, 2011
Web Log - July, 2011
Web Log - June, 2011
Web Log - May, 2011
Web Log - April, 2011
Web Log - March, 2011
Web Log - February, 2011
Web Log - January, 2011
Web Log - December, 2010
Web Log - November, 2010
Web Log - October, 2010
Web Log - September, 2010
Web Log - August, 2010
Web Log - July, 2010
Web Log - June, 2010
Web Log - May, 2010
Web Log - April, 2010
Web Log - March, 2010
Web Log - February, 2010
Web Log - January, 2010
Web Log - December, 2009
Web Log - November, 2009
Web Log - October, 2009
Web Log - September, 2009
Web Log - August, 2009
Web Log - July, 2009
Web Log - June, 2009
Web Log - May, 2009
Web Log - April, 2009
Web Log - March, 2009
Web Log - February, 2009
Web Log - January, 2009
Web Log - December, 2008
Web Log - November, 2008
Web Log - October, 2008
Web Log - September, 2008
Web Log - August, 2008
Web Log - July, 2008
Web Log - June, 2008
Web Log - May, 2008
Web Log - April, 2008
Web Log - March, 2008
Web Log - February, 2008
Web Log - January, 2008
Web Log - December, 2007
Web Log - November, 2007
Web Log - October, 2007
Web Log - September, 2007
Web Log - August, 2007
Web Log - July, 2007
Web Log - June, 2007
Web Log - May, 2007
Web Log - April, 2007
Web Log - March, 2007
Web Log - February, 2007
Web Log - January, 2007
Web Log - December, 2006
Web Log - November, 2006
Web Log - October, 2006
Web Log - September, 2006
Web Log - August, 2006
Web Log - July, 2006
Web Log - June, 2006
Web Log - May, 2006
Web Log - April, 2006
Web Log - March, 2006
Web Log - February, 2006
Web Log - January, 2006
Web Log - December, 2005
Web Log - November, 2005
Web Log - October, 2005
Web Log - September, 2005
Web Log - August, 2005
Web Log - July, 2005
Web Log - June, 2005
Web Log - May, 2005
Web Log - April, 2005
Web Log - March, 2005
Web Log - February, 2005
Web Log - January, 2005
Web Log - December, 2004
Web Log - November, 2004
Web Log - October, 2004
Web Log - September, 2004
Web Log - August, 2004
Web Log - July, 2004
Web Log - June, 2004