
Dynamics

|
Generational Dynamics |
| Modern Generational Theory | |
| HOME WEB LOG COUNTRY STUDIES COMMENT FORUM | |
| DOWNLOADS FOURTH TURNING ARCHIVE ABOUT | |
The political power of Amazon, Apple, Facebook, Google and Microsoft
by
John J. Xenakis
This morning's key headlines from GenerationalDynamics.com
 |
There was a major news story recently that you may have missed about an extremely serious hacking breach.
Last month, hackers took control of dozens of Twitter accounts, and used them to try to extort hundreds of thousands of dollars from millions of Twitter users. The hackers used a very simple "low tech" technique to gain control: they bribed or extorted or tricked a Twitter employee to giving them control. There are undoubtedly hundreds or even thousands of people in Twitter's IT department with full access to the user databases who could have satisfied the hackers, although Twitter is now thought to be reducing that number.
When this happened, most people were shocked that this could even happen. Most thought that it was impossible. In this article, we're going to show that this and a lot worse can happen to Microsoft and other online services.
According to Twitter:
"The attackers successfully manipulated a small number of employees and used their credentials to access Twitter’s internal systems, including getting through our two-factor protections. As of now, we know that they accessed tools only available to our internal support teams to target 130 Twitter accounts. For 45 of those accounts, the attackers were able to initiate a password reset, login to the account, and send Tweets. We are continuing our forensic review of all of the accounts to confirm all actions that may have been taken. In addition, we believe they may have attempted to sell some of the usernames."
News reports at the time speculated that the Twitter attack was just a rehearsal for a much larger attack by Russia or China to be launched just prior to the November 3 election, to influence the election.
According to press reports, all the hackers wanted was money, but press reports speculate that they could have been a lot more malicious, and the recent attack could have been a practice test for a more extensive attack to manipulate the November 3 elections.
According to Sen. Richard Blumenthal (D-Conn.):
"This hack bodes ill for November balloting. Count this incident as a near miss or shot across the bow. It could have been much worse with different targets. So many security red flags are raised by this criminal attack that the culprits should be tracked down as quickly as possible."
Blumenthal is right about the large number of security red flags. But he's wrong that the problem can be solved by tracking down the culprits. The reason he's wrong is that this is a simple, low-tech attack. There's no super-complex hacking software involved. It's done the old fashioned way, with bribery and extortion or tricking of Twitter employees.
And the same low-tech attack could be used on any of the online giants -- Google, Amazon, Facebook, or Microsoft or indeed on any large online service. A malicious actor, including a country like China or Russia, could use bribery or extortion to "manipulate" one or more IT employees to gain access to or control of dozens or hundreds or even thousands of user accounts or computers. This is what happened at Twitter, and it can happen at any of the online giants. How the malicious actor uses that access or control varies from one online giant to another, but the core technique of using bribery or extortion to gain control is the same in all cases.
In this article, we're going to focus on Microsoft. According to Microsoft, there are almost one billion desktop computers running Windows 10. Microsoft is a monopolist with complete control of Windows 10 on those one billion computers. Microsoft can update or modify the Windows 10 software at any time, and there's nothing that any user can do to stop it because, for almost all users, there's no other choice but to use Windows 10. Microsoft is the quintessential monopolist, with total control of a product that one billion people are forced to use.
We're going to show how Microsoft illegally uses its monopoly power to extort money from users. The method is obvious from the numbers: If Microsoft can update or modify the Windows 10 software on computers in order to "coerce" a million users to pay $100 each for Microsoft apps or services or upgrades, then Microsoft makes $100 million for doing essentially nothing. This is the essense of monopoly power.
We're going to show how Microsoft is already doing that, and we're going to show how a malicious actor, like Russia or China, could use an attack similar to the Twitter hack to extort money or even to start a war.
Let's begin by giving three examples of how this has already occurred in other ways.
It's estimated that some 3 billion iPhones have been sold, and Apple has the kind of monopolistic control over them that Microsoft has over Windows. Apple has already used criminal monopolistic behavior to force users of older iPhones to upgrade.
You may recall from March that Apple was forced to pay up to $500 million to settle a US lawsuit. Apple had used its monopolistic control over iPhones to slow down old iPhones, in order to coerce users into upgrading. This is criminal behavior under the antitrust laws, and that's why Apple was forced to settle, and was anxious to settle. They were lucky that it cost them only $500 million.
Here are some excerpts from a Reuters news story from March:
"Apple to pay up to $500 million to settle U.S. lawsuit over slow iPhones(Reuters) - Apple Inc has agreed to pay up to $500 million to settle litigation accusing it of quietly slowing down older iPhones as it launched new models, to induce owners to buy replacement phones or batteries.
Consumers contended that their phones’ performance suffered after they installed Apple software updates. They said this misled them into believing their phones were near the end of their lifecycles, requiring replacements or new batteries.
Apple attributed the problems mainly to temperature changes, high usage and other issues, and said its engineers worked quickly and successfully to address them. Analysts sometimes refer to the slowing of iPhones as “throttling.”
Following an initial outcry over slow iPhones, Apple apologized and lowered the price for replacement batteries to $29 from $79."
Apple was committing a crime by using its monopoly control of iPhones to force iPhones to run more slowly, in order to coerce the user to upgrade to a new iPhone. That's why Apple was desperate to settle as quickly as possible.
An important part of Apple's behavior is that it must be as obscure as possible to the user. If the user knew that Apple was purposely throttling his iPhone, he might trade it in for an Android. Instead, slowing the iPhone down is made as obscure and invisible as possible so that the user doesn't know what's going on, and just buys a new iPhone.
I realize that many people idolize Tim Cook and Apple, but this is incredibly sleazy behavior. Apple managers are screwing their own customers to essentially extort their customers to buy new iPhones. It's absolutely incredible, but it shows the state of corporate management these days. Apple managers like Tim Cook and Craig Federighi are criminals who are totally lacking in morality and ethics. And this criminal behavior actually happened.
But with 3 billion iPhones under their control, morality and ethics go out the window, as Cook and Federighi look for ways to extort more cash from users. The chance to extort billions of dollars from users is just too tempting.
If anyone reading this wants to argue that Microsoft managers are less unethical and immoral than Apple managers, then I'd like to hear that argument.
Example #1 was Apple's illegal throttling hack on iPhones to slow them down, forcing users to upgrade.
Example #2 is an illegal action in 2016 by Microsoft to force Windows Pro users to upgrade to Windows Enterprise, costing as much as $200 for each user.
In July 2016, Microsoft updated Windows 10 on its customers' desktop to make it impossible for Windows Pro users to eliminate Windows crapware like games, ads, trials and teasers. Users already have to pay a big premium to run Windows Professional, but they do so because, well, they're professionals like me, and want a professional version of Windows, so they want the option of removing things like games. But that's not good enough for Microsoft. Microsoft wants to force Pro users to pay $100-200 more per computer to get the professional features they thought they already had.
Here is a July 28, 2016, post by Russian blogger Sergey Tkachenko on his Winaero blog:
"Microsoft locks some Group Policy options to Enterprise editions in Windows 10 Anniversary UpdateToday, we surprisingly discovered that Microsoft has secretly changed the availability of some Group Policy options in Windows 10 version 1607. Windows 10 version 1607 "Anniversary Update" has reduced the control via Group Policy that you have in Pro edition. Pro edition users have lesser options available compared to version 1511, so many behaviors of the OS cannot be controlled.
If you open the Group Policy management console and read the description of certain policy settings in Windows 10 build 14393, you will find out that the options mentioned below are NO LONGER AVAILABLE for Windows 10 Pro users. They are locked down to Enterprise and Education editions only: ...
Turn off Microsoft consumer experiences. Using this option, you could prevent Windows 10 from automatically downloading and installing promoted apps like Candy Crush Soda Saga, Flipper, Twitter, NetFlix, Pandora, MSN News and many other potentially unwanted apps and games. Now you can't prevent these apps from being automatically downloaded and installed if you are using Windows 10 Pro or Home editions. The policy setting (or Registry setting) has no effect in these editions. consumer experience Starting with Windows 10 Anniversary Update, you can only control unwanted apps in Enterprise and Educations editions of Windows 10. This behavior was confirmed when I upgraded my Windows 7 Professional to Windows 10 Pro and many unwanted apps installed automatically from the Store."
A Zdnet article by Mary Jo Foley at that same time explains why Microsoft did this:
"Why did Microsoft remove the ability for admins to change and shut off these apps and settings? I asked and didn't hear back from company officials.Some of us cynics believe the change was because Microsoft wants to get more users to upgrade to the more expensive Enterprise SKU. ...
Microsoft officials have been very up front about looking for ways to make money indirectly from Windows 10 in various ways, including promotional/sponsored app suggestions. ... The Softies are trying to push more people to go to the Store and download new/more apps. Microsoft gets a cut of third-party apps downloaded from the Store."
This is pretty much a smoking gun. Microsoft wants to prevent Pro users from stopping the crapware attacks, so the option to stop them is disabled in the Pro edition. Foley call the Microsoft execs "softies," but I would call them hardcore monopolistic criminals.
This is clearly extortionary behavior by Microsoft that's illegal. There is absolutely no reason to remove these options from the Pro version, except to extort money from users who are trapped by Microsoft's monopoly, and have already paid a premium for the "Professional" version of Windows 10.
Like many sophisticated users, I used to love my Windows-7 system. It worked great, with none of the Microsoft crap that you have to put up with in Windows-10.
In mid-January 2019, on a Tuesday afternoon, all of a sudden my Windows 7 computer started getting incredibly slow. Firefox was brought to its knees, and Chrome was working intermittently.
I spent many days trying to figure out which process was causing the problem, and then I realized that it was far more sinister: Whenever I started using Firefox, or a Youtube video on Chrome, or Windows Media Player, or any of several other programs, then the problem would occur. What would happen is that that particular program would only use 15-20% of the cpu, but Windows would magically jack up the CPU usage of other normally innocuous processes.
So for example, when the system was mostly idling, process explorer might show the top cpu users as omnipage 1.3%, firefox 0.9%, sidebar 0.9%, emacs 0.1%, acro rd32 0.3%, and so forth, totalling around 10%.
But when I started up a youtube video on chrome, that process would use 23% of the cpu, which wouldn't be a problem. But all of those numbers in the last paragraph were now jacked up to 13.1%, 8.4%, 5.6%, and so forth, totaling 100%, bringing the system to its knees.
In other words, starting up something on Chrome or Media Player or any of numerous other programs would affect every other process on the system. For example, I open Media Player, and suddenly Emacs would go from using 0.1% of the cpu to 13.1% of the cpu, which makes no sense at all.
So I started searching the internet, and I found that it's happening to other people. Apparently it was triggered by a particular windows update. Being a paranoid individual, I took note of the fact that this problem started occurring the same week that Microsoft reminded everyone that Windows 7 support would expire in a year, and I wondered if this was a Microsoft plot to force people to install Windows 10.
What was going on was purposely obscure to 99.9% of the Windows-7 users. I'm one of the few users who could figure out what was going on, since I spent many years of my career developing operating systems. I developed three embedded operating systems, and two mainframe operating systems, so I'm very capable of diagnosing these situations.
So after a great deal of analysis, I knew that the only way this problem could be occurring would be is if someone (Microsoft) changed the operating system in a certain way. There's a process queue in the core of any timesharing operating system, and there's a core o/s function that takes the top process off the queue and gives it a time slice -- let's it execute for a few milliseconds. When the time slice expires, then that process goes on the bottom of the process queue, and the new top of queue is allowed to run for a time slice. That's how the operating system makes it appear that multiple programs are all running simultaneously when, in fact, they are running in turn, a few milliseconds at a time.
So the problem I was having could happen only one way: Microsoft had modified the operating system on my computer to add several milliseconds of time in a do-nothing loop to each time slice for each process. This might have been simply a bug, and that's why I was hoping that it would be corrected in the next Windows update. But it wasn't corrected in the next update or the one after. It was clear to me that that Microsoft was doing this on purpose, to force me to upgrade to Windows 10.
By the way, the only reason I could figure this out was because of my years of operating system experience. Ordinary users would have no clue what was going on, and that's how Microsoft wanted it. And if they called anyone for support, they would simply be told that their computer was getting too old, and they should upgrade to Windows 10.
I knew what was going on, but it didn't matter. Microsoft is a powerful monopolist that can screw me or any of its users at any time of its choosing, to extract money or whatever. After a few weeks of despair, I bought a new Dell Windows-10 computer. Then, of course, Microsoft started with crapware downloads on my new computer, which caused the same kind of performance problem as on my old computer.
I've now given three examples of illegal monopolistic behavior -- Apple throttling iPhones, Microsoft forcing upgrade to Enterprise edition, and Microsoft forcing upgrade from Windows 7 to Windows 10. All of these are examples are of a monopolistic company illegally using its monopoly power to extort money from users.
We'll now turn to the particular subject of this article, Microsoft's illegal monopolistic behavior downloading crapware. However, this example is much worse because unlike the recent Twitter hack, it's about more than money.
At any time of the day or night, Microsoft downloads several gigabytes of data to my computer, essentially crippling my computer. If I'm trying to get some work done, then I'm screwed. Response time to a simple command becomes 15-30 seconds, and saving a file in an Emacs editor can sometimes take as much as 5 minutes.
The crapware downloads are different from the regular Windows Updates downloads. Those updates occur at scheduled times, and they're carefully controlled by Microsoft procedures that have been developed for years.
However, with Windows 10, that hasn't been enough for Microsoft. Every week, Microsoft downloads several gigabytes of ads, games, videos and other crapware to your computer in a completely uncontrolled fashion. These downloads go on for hours, often completely crippling the desktop computer being targeted.
My experience for the last year is that Microsoft cripples my computer at any time of the day or night, for any number of hours at a time, to store more crapware on my computer. To say that this infuriates me would be a big understatement.
Let me make it clear that I don't care about the ads. I'm used to seeing ads on tv, on web sites, in magazines, and so forth. That's not the problem. The problem is that Microsoft is purposely crippling my computer at any time, for hours at a time, to download their crapware, preventing me from getting my work done. This is criminal behavior by a monopolist, designed to force users to upgrade or to purchase additional Microsoft services.
As a Senior Software Engineer of many decades, I can spot bad software and sloppy implementations. Here's a list of the characteristics of these crapware downloads that reveal the intent:
As a software engineer of many decades, I see the above list as proof that Microsoft is purposely screwing its users for financial gain, just as Apple did in throttling iPhones. Some of the items in the above list could be fixed trivially, such as displaying advance notifications, and allowing the user to reschedule, or lowering the priority of the process, so that the computer isn't crippled. The fact that Microsoft designed these downloads to do the greatest possible harm to its own users in the most chaotic way is proof, in my opinion, of extreme malice and criminal behavior on the part of Microsoft.
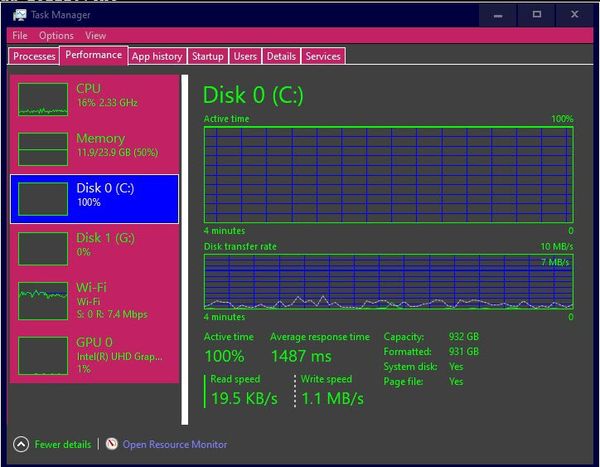
For most users, it's almost impossible to see what's going on, except that your computer slows down. The only way that I know of to see what's happening during a crapware download is to open the Task Manager, go to the performance tab, and click on the "Disk 0 (C:)". You'll see that disk activity is solid 100% without variation, sometimes for hours. (By the way, I've gotten into the habit of leaving the Task Manager window open all the time to that tab. If I'm suddenly having problems, I can click on that window, and usually I can see that a new Microsoft crapware attack is just beginning.)
The graphic at the beginning of this article shows what Task Manager looks like during a crapware attack. Note that the Drive C: activity is at 100%, and this can go on for minutes or hours. That's on the Performance tab. If you try to switch back to the Process tab, you'll see that there's nothing going on -- Microsoft has purposely hidden the crapware download activity so that you can't plan for it or modify it, or even know it's going on. Microsoft can do this because it's a monopoly and it has control of your computer, and can do whatever it wants to you.
As a Software Engineer, I've always had a very high opinion of Windows, and Microsoft technology. I started playing around with Windows version 1 in 1985. Since then, I haven't always agreed with some of the directions that Windows took, but I always felt that they were intended to be in the best interest of the users. Until a year or two ago, Windows was always a gold star product, in my opinion.
I also met Bill Gates two or three times in the 1990s. I thought he was a really decent, competent guy who, once again, believed in doing what was in the best interest of the users.
But Bill Gates is gone now, having left Microsoft years ago to save the world from malaria and coronavirus. The company that he left behind has turned into a sewer with a corporate culture of young people who happily sacrifice the best interest of their users for their own agendas and money.
I'm now ready to show how Microsoft's policies risk a global hacking attack on Microsoft that can have much more serious consequences than the similar attack that's already occurred on Twitter.
I've now shown the following:
With regard to "manipulating" any of the employees of these services, let's recall that there are hundreds of thousands of Chinese living in America. Under Chinese law, the Chinese military tracks them and requires them to provide intelligence or perform other duties as described by the military. China's 2017 National Intelligence Law requires all Chinese citizens and businesses to perform such duties, even when doing so is illegal. I don't blame the Chinese citizens for this. I blame the Chinese Communist thugs who treat their own citizens like dirt, as contrast to ethnic Chinese citizens who live in Taiwan and have much higher standards of living, much more freedom, and aren't persecuted by a paranoid, desperate government.
The major online services are mostly headquartered in the west, and so have many Chinese employees. These people are all subject to China's National Intelligence Law, and so they can be directly "manipulated" by China's military. If one of these employees has access to the company's user database -- and I have no doubt that many do -- then those employees can be "manipulated" into stealing data, stealing accounts, or taking control of millions of users' accounts, as has already happened in the case of the Twitter hack.
I have a personal anecdote related to this subject. A few months ago, I started receiving robocall phone messages in Chinese on my home phone. So I recorded one of them and asked someone to translate. It went: "Hello, this is the Chinese embassy. You have a very important notification. For details please press xxx." So I don't know why my phone number was called, or what sort of "important notification" was intended, but this shows one of the ways that the Chinese Commuists keep Chinese people in America on a short leash, ready to do as they're told.
On July 29, 2020, the House Judiciary committee held a hearing on examining the dominance of Amazon, Apple, Facebook, and Google. The CEOs of all four companies came and testified, and were questioned by the politicians on the committee.
The hearing began in full-scale farce. The opening statement of Jeff Bezos, CEO of Amazon, began as follows:
"My mom, Jackie, had me when she was a 17-year-old high school student in Albuquerque, New Mexico. Being pregnant in high school was not popular in Albuquerque in 1964. It was difficult for her. When they tried to kick her out of school, my grandfather went to bat for her. After some negotiation, the principal said, “OK, she can stay and finish high school, but she can’t do any extracurricular activities, and she can’t have a locker.” My grandfather took the deal, and my mother finished high school, though she wasn’t allowed to walk across the stage with her classmates to get her diploma."
Listening to this, I was soooooooo touched that I almost had tears streaming down my face. It was just so sad.
Sundar Pichai, CEO of Alphabet Google, took a slightly different approach:
"Expanding access to opportunity through technology is deeply personal to me. I didn’t have much access to a computer growing up in India. So you can imagine my amazement when I arrived in the U.S. for graduate school and saw an entire lab of computers I could use whenever I wanted. Accessing the internet for the first time in that computer lab set me on a path to bring technology to as many people as possible. It’s what inspired me to join Google 16 years ago."
Once again, very touching.
So what's going on here? These ridiculous statements are carefully planned and carefully rehearsed well in advance, in both content and demeanor, to show that these huge online service monopolies are really just innocent little businesses, bringing the American dream to millions of others.
It's as if to say, "We're not like other wicked monopolists -- John D. Rockefeller in oil, Andrew Carnegie in steel, Cornelius Venderbilt in railroads. Those are nasty, mean, old, ancient, out-of-date monopolies. Not like us. We're sweet, happy, modern, hip, cool monopolies, and we're different."
The CEOs were playing on the politicians' ignorance and stupidity, which is trivially easy. The objective of the CEOs was to avoid answering any real questions from the posturing politicians, who are too dumb to know what was going on anyway, since they barely know how to turn on a computer. And it worked.
So what are the questions that the CEOs were afraid to answer?
One of them was the one we've been discussing. This hearing occurred shortly after the Twitter hack, and the CEOs were undoubtedly all dreading the question: "Could the same thing happen to you?" They were dreading that question because the answer would have to have been "Yes," although they would have buried that answer in multiple paragraphs of self-excusing verbiage.
The second question the CEOs are afraid to answer is about their censorship monopoly.
This article has been about illegal abuse of monopoly power and exposure to data breaches, by the large online services, especially Microsoft.
However, with the November 3 presidential election approaching, we're seeing abuse of a different kind of monopoly power. We're seeing Google, Facebook and Twitter abuse their monopoly power over censorship to influence the election toward the Democrats by censoring anything from Trump's 63 million supporters as "hate speech" or "fake speech." There are many examples of this that are extremely ridiculous, such as approving support for left-wing protests and violent riots by antifa, while condemning street protests against Democratic governors as racist or dangerous.
Ironically, this didn't start with Trump's presidency and actually has nothing to do with Trump. It was already going on early in the Obama administration with the vitriolic attacks by Democrats on members of the conservative Tea Party, referring to Teapartiers with the hate term "teabaggers," which is as bad as the N-word. In my almost 20 years of developing Generational Dynamics, I've seen many similar examples of one group hating another group for no reason at all. I don't know what chromosome or hormone causes this, but I do know that that chromosome or hormone causing Democrats to hate 63 million Teapartiers and Trump supporters is exactly the same as the one that caused the Nazis to hate the Jews, the Hutus to hate the Tutsis, or the Chinese Communists to hate the Uighurs and Tibetans. This is a constant of human nature, and we're seeing it played out in America today in the Democrats' vitriolic hatred of 63 million Teapartiers and Trump supporters.
So today we have the major online services -- Google, Facebook and Twitter -- supporting this hatred by classifying anything by Teapartiers or Trump supporters as "hate speech" or "fake speech."
When confronted with evidence of this, a standard answer is to appeal to the magic of artificial intelligence. "The decision whether something is hate speech is made by impersonal AI algorithms in computers that are non-partisan and not political. Haha."
Politicians who barely know how to turn on a computer just accept this argument, as if there were some magic involved. Actually, there's no magic involved. AI algorithms like that are rules-driven, and programmers would write the rules.
The rules used by Google and others are confidential, of course, but we can speculate on how some of them work. Let's suppose a tweet contains the text, "Make America great." That alone wouldn't be enough to classify it as hate speech, but it would add points in some sort of point system. If a tweet contains another "racist" phrase like that, then there might be enough points for the "non-partisan" algorithms to decide that the tweet is hate speech.
Who decides what these rules are? The deciders are Google employees. Among the Google employees making the rules there will be women as well as men, to prevent anti-female bias in the rule-making. And there will be blacks as well as whites, in order to prevent anti-black bias in the rule-making. But what do they do about anti-conservative bias? The answer is NOTHING. We know from various statements and blogs and leaked meeting videos that all the employees at Google are far left, and if there are any politically moderate employees at Google (such as James Damore), they will be fired or marginalized by the others, and their suggestions for rules will ignored in group code reviews.
So we have a situation where Google is fully on-board to target 63 million tea partiers and Trump supporters in order to affect the November 3 election. As I said, for one demographic group to hate another demographic group is common throughout history and the world, as in the Nazi hatred of Jews and the Hutu hatred of Tutsis or any of a million other examples that anyone who studies history can name. The one good thing we can say about the current situation is that the hate campaign has not yet degenerated into genocide, although genocide is the stated objective of the fascist organization antifa.
I can't end this article without looping back to the beginning.
There are some important points to be made about the power of monopoly. I've shown how companies like Apple and Microsoft use their monopoly power to coerce millions of users to purchase additional unnecessary services, products and upgrades, making hundreds of million or billions of dollars for the companies involved, or how Google, Twitter and Facebook are using their monopoly power over censorship rules to control the November 3 elections.
But I've also shown the danger of monopoly -- to the companies, to the country, and even globally. Think of a monopoly as an enormous source of power that the company can use in many ways to make money. But now suppose a malicious actor, like Russia or China, finds a way to gain control of that enormous power, as has already happened in the case of the Twitter hack. That power then becomes a weapon that can destroy the company, destroy million of lives or businesses, or destroy a country.
Right now that monopoly power is being used to make money and to affect the November 3 election. But we can also be certain that hackers around the world have learned from the Twitter hack, and are working 24 hours a day to gain control of an online system for their own financial or political benefit. It's possible that they've already succeeded without our knowing it.
In the middle of an election season, it's too late to even think about fixing this problem this year. But fixing this problem should be among the highest government priorities next year, no matter who wins the election.
(Comments: For reader comments, questions and discussion,
see the Generational Dynamics World View News thread of the Generational
Dynamics forum. Comments may be posted anonymously.)
(17-Aug-2020)
Permanent Link
Receive daily World View columns by e-mail
Donate to Generational Dynamics via PayPal
Web Log Summary - 2020
Web Log Summary - 2019
Web Log Summary - 2018
Web Log Summary - 2017
Web Log Summary - 2016
Web Log Summary - 2015
Web Log Summary - 2014
Web Log Summary - 2013
Web Log Summary - 2012
Web Log Summary - 2011
Web Log Summary - 2010
Web Log Summary - 2009
Web Log Summary - 2008
Web Log Summary - 2007
Web Log Summary - 2006
Web Log Summary - 2005
Web Log Summary - 2004
Web Log - December, 2020
Web Log - November, 2020
Web Log - October, 2020
Web Log - September, 2020
Web Log - August, 2020
Web Log - July, 2020
Web Log - June, 2020
Web Log - May, 2020
Web Log - April, 2020
Web Log - March, 2020
Web Log - February, 2020
Web Log - January, 2020
Web Log - December, 2019
Web Log - November, 2019
Web Log - October, 2019
Web Log - September, 2019
Web Log - August, 2019
Web Log - July, 2019
Web Log - June, 2019
Web Log - May, 2019
Web Log - April, 2019
Web Log - March, 2019
Web Log - February, 2019
Web Log - January, 2019
Web Log - December, 2018
Web Log - November, 2018
Web Log - October, 2018
Web Log - September, 2018
Web Log - August, 2018
Web Log - July, 2018
Web Log - June, 2018
Web Log - May, 2018
Web Log - April, 2018
Web Log - March, 2018
Web Log - February, 2018
Web Log - January, 2018
Web Log - December, 2017
Web Log - November, 2017
Web Log - October, 2017
Web Log - September, 2017
Web Log - August, 2017
Web Log - July, 2017
Web Log - June, 2017
Web Log - May, 2017
Web Log - April, 2017
Web Log - March, 2017
Web Log - February, 2017
Web Log - January, 2017
Web Log - December, 2016
Web Log - November, 2016
Web Log - October, 2016
Web Log - September, 2016
Web Log - August, 2016
Web Log - July, 2016
Web Log - June, 2016
Web Log - May, 2016
Web Log - April, 2016
Web Log - March, 2016
Web Log - February, 2016
Web Log - January, 2016
Web Log - December, 2015
Web Log - November, 2015
Web Log - October, 2015
Web Log - September, 2015
Web Log - August, 2015
Web Log - July, 2015
Web Log - June, 2015
Web Log - May, 2015
Web Log - April, 2015
Web Log - March, 2015
Web Log - February, 2015
Web Log - January, 2015
Web Log - December, 2014
Web Log - November, 2014
Web Log - October, 2014
Web Log - September, 2014
Web Log - August, 2014
Web Log - July, 2014
Web Log - June, 2014
Web Log - May, 2014
Web Log - April, 2014
Web Log - March, 2014
Web Log - February, 2014
Web Log - January, 2014
Web Log - December, 2013
Web Log - November, 2013
Web Log - October, 2013
Web Log - September, 2013
Web Log - August, 2013
Web Log - July, 2013
Web Log - June, 2013
Web Log - May, 2013
Web Log - April, 2013
Web Log - March, 2013
Web Log - February, 2013
Web Log - January, 2013
Web Log - December, 2012
Web Log - November, 2012
Web Log - October, 2012
Web Log - September, 2012
Web Log - August, 2012
Web Log - July, 2012
Web Log - June, 2012
Web Log - May, 2012
Web Log - April, 2012
Web Log - March, 2012
Web Log - February, 2012
Web Log - January, 2012
Web Log - December, 2011
Web Log - November, 2011
Web Log - October, 2011
Web Log - September, 2011
Web Log - August, 2011
Web Log - July, 2011
Web Log - June, 2011
Web Log - May, 2011
Web Log - April, 2011
Web Log - March, 2011
Web Log - February, 2011
Web Log - January, 2011
Web Log - December, 2010
Web Log - November, 2010
Web Log - October, 2010
Web Log - September, 2010
Web Log - August, 2010
Web Log - July, 2010
Web Log - June, 2010
Web Log - May, 2010
Web Log - April, 2010
Web Log - March, 2010
Web Log - February, 2010
Web Log - January, 2010
Web Log - December, 2009
Web Log - November, 2009
Web Log - October, 2009
Web Log - September, 2009
Web Log - August, 2009
Web Log - July, 2009
Web Log - June, 2009
Web Log - May, 2009
Web Log - April, 2009
Web Log - March, 2009
Web Log - February, 2009
Web Log - January, 2009
Web Log - December, 2008
Web Log - November, 2008
Web Log - October, 2008
Web Log - September, 2008
Web Log - August, 2008
Web Log - July, 2008
Web Log - June, 2008
Web Log - May, 2008
Web Log - April, 2008
Web Log - March, 2008
Web Log - February, 2008
Web Log - January, 2008
Web Log - December, 2007
Web Log - November, 2007
Web Log - October, 2007
Web Log - September, 2007
Web Log - August, 2007
Web Log - July, 2007
Web Log - June, 2007
Web Log - May, 2007
Web Log - April, 2007
Web Log - March, 2007
Web Log - February, 2007
Web Log - January, 2007
Web Log - December, 2006
Web Log - November, 2006
Web Log - October, 2006
Web Log - September, 2006
Web Log - August, 2006
Web Log - July, 2006
Web Log - June, 2006
Web Log - May, 2006
Web Log - April, 2006
Web Log - March, 2006
Web Log - February, 2006
Web Log - January, 2006
Web Log - December, 2005
Web Log - November, 2005
Web Log - October, 2005
Web Log - September, 2005
Web Log - August, 2005
Web Log - July, 2005
Web Log - June, 2005
Web Log - May, 2005
Web Log - April, 2005
Web Log - March, 2005
Web Log - February, 2005
Web Log - January, 2005
Web Log - December, 2004
Web Log - November, 2004
Web Log - October, 2004
Web Log - September, 2004
Web Log - August, 2004
Web Log - July, 2004
Web Log - June, 2004